Reliable, secure, compliant.
Ensure your data is safe with the highest standards of data security
Talk to sales

The ultimate care for your data.
Store data securely with at rest encryption
Passwords are digitally signed with sha256 and unique salts.
Transmit data securely with SSL
Secure Socket Layer (SSL) is an industry-standard for securing and encrypting data transmission.
Prevent DDoS and other attacks with single-tenancy
On Xano's dedicated resource plans, the user's instance is on a single-tenant deployment or architecture.
Learn how to secure
your data with Xano
Download Ebook

Secure your backend
Xano is built to help citizen developers scale their backend, using technologies like Docker, Kubernetes, and Google Cloud.
Workspace / Role based access control
Login authentication
Password encryption
Password requirements
2FA security
Inactivity timeout

Stay in control
RBAC (Role-based access control) or role-based permissions is a way to restrict access based on a user's defined role.
Workspace / Role based access control

Stay in control
RBAC (Role-based access control) or role-based permissions is a way to restrict access based on a user's defined role.
Login authentication

Customizable login processes
Authentication is the way the backend handles adding users and allowing them to access certain areas of your app.
Password encryption
Password requirements

Strong passwords
A password must be a minimum of eight (8) characters, maximum of 256 characters, at least one (1) alphabetic character, and at least one (1) numeric character.
2FA security

Additional layer of security
2FA security requires the use of two different forms of identification to access and authenticate an account.
Inactivity timeout

Protect your privacy
An inactivity timer which will log you out after 2 hours of inactivity. This can be adjusted or disabled entirely via your account settings.
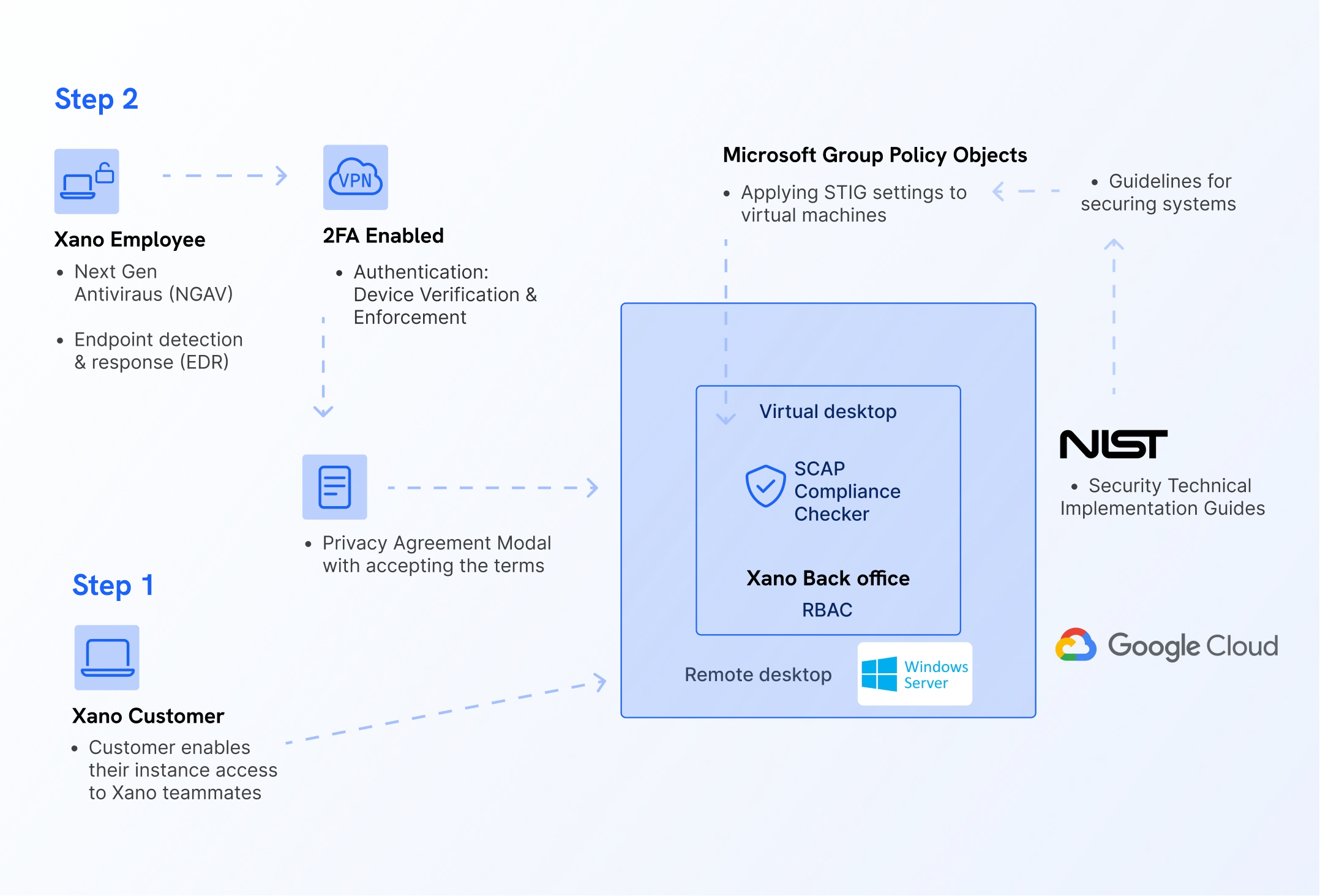
Secure Data Access Procedure (SDAP)
A two-step Secure Data Access Procedure (SDAP), requiring customer-enabled access and strict internal protocols. Governed by Role-Based Access Controls (RBAC), this makes sure data is accessed on a need-to-know basis, adhering to the principle of least privilege (PoLP).
Security & compliance certifications

ISO 27000 Series
The ISO 27000 Series sets standards for information security and privacy, including ISO 27001 and ISO 27701 for trusted data protection.

ISO 42001
ISO 42001 is the first global standard for responsible AI implementation, defining frameworks for ethical, transparent, and trustworthy AI management.

ISO 9001
ISO 9001:2015 serves as the quality benchmark of organizations located across the globe.

SOC 2
SOC 2 is an internal control report capturing how a company safeguards customer data and how well those controls are operating.

GDPR
GDPR is a European regulation ensuring lawful, transparent, and secure processing of personal data.

HIPAA
HIPAA (1996) is a set of regulations governing the use and disclosure of protected health information.

HDS
HDS certifies secure hosting of health data, ensuring confidentiality and compliance with France’s healthcare regulations.

CPRA
Safeguards for sensitive data including location, demographics, beliefs, affiliations, communications, genetics, sexuality, and health related records.

FERPA
FERPA gives parents rights over their children's education records. These rights transfer to students at age 18 or when they attend post-secondary school.

CCPA
The California Consumer Privacy Act (CCPA) is a state statute intended to enhance privacy rights and consumer protection for residents of California, United States.

LGPD
The LGPD sets rules for handling personal data in Brazil, applying to both domestic and foreign entities processing Brazilians' data.

PIPEDA
A Canadian federal law from 2000 regulating personal information handling in commercial activities nationwide, except where provinces have similar laws.
Frequently asked questions
Yes. Xano complies by utilizing the following open source licenses of: PHP 8, Node.js, PostgreSQL, Angular 17, and Redis 7.2.
It does not come standard. It is only possible if enabled through our Enterprise Edition.
Yes, Xano integrates SAST into its development process to analyze source code for vulnerabilities. This approach enables the early detection of security issues during the coding phase. By utilizing automated tools, Xano can identify potential vulnerabilities, such as SQL injection, cross-site scripting (XSS), and insecure coding practices.
Each of our database types (i.e. text, int, decimal, boolean, etc) have their own built-in filters to validate their input. When assigning a type to a database column or input variable, you can rely on the contents of that variable to have successfully passed the appropriate input validation for that specific type.
Xano requires all web communication over HTTPS TLSv1.2 or above.
Xano currently supports the following regions: Australia, Belgium, Brazil, Canada, France, Germany, India, Indonesia, Japan, Saudi Arabia, Singapore, South Korea, Switzerland, the United Kingdom, and the United States.
Yes, using Redis is mandatory. Xano uses it for caching various parts of the application schema. It is also used for API/function caching (if enabled) and it is accessible within our function stack.
Multi-zone configurations are supported through our Enterprise BYOC offering. It is not supported through the traditional SaaS plans.
Code is verified using Snyk.
Xano allows you to set rate limits on your queries so that you can limit the requests per given time period that an API endpoint can be called. The Rate Limit function comes with a few settings for configuration.
Upon discontinuing Xano services, you retain the capability to export all data from your Xano account(s). You maintain complete control over the data utilized within your instances. However, it's important to note that any code associated with your Xano setup is not exportable.
Yes, Xano provides support for background tasks (cron jobs), allowing them to execute concurrently. Moreover, the resources allocated for background tasks are segregated from those designated for API operations.